You may be receiving fake emails from your contacts. They may be more common than you think. So, you may be asking yourself if the message you received was really from a friend. This article will help you identify emails sent by your contact list and those sent by scammers.
Spam emails from your contacts are from scammers spoofing email addresses from your contact list. These emails are not really coming from your friends and family. Emails addresses are being faked to make it more likely you will respond to a scam.



When I was younger, my mom received a letter from a friend recommending a weight loss program. She took offense to this and was thinking her friend was implying she was overweight. Fortunately, my dad caught wind of the situation and explained everything. “It’s a scam! It’s a scam”. I can still remember him exclaiming.
It was a clever marketing tactic making it seem like a personal recommendation for a business. Back then, it was probably thought of as a cutting-edge marketing strategy. This happened before internet marketing was as popular as it is now. But this same thing is happening today. Instead of a letter in the mail, it comes in the form of an email.
Table of Contents
Spoofing Meaning
They say that imitation is the sincerest form of flattery. However, when it comes to spoofing, it is not very complimentary. To spoof is to mimic. When it comes to email spoofing, what this means is that a message is sent that appears to be from one source. But it is originating from a different person. This different person is the scammer or spammer.
When you receive spam emails, you may not be able to tell if it is a spoofed email based on face value. That is the point. When you look at the sender, it truly appears as though one identifiable person sent the email.
However, with some digging and technical skills, you may be able to see in the background looking at the code that the source is not the same as what it appears to be.
In the film industry, a spoof is a parody. For example, the movie Scary Movie is a spoof of the blockbuster hit Scream.
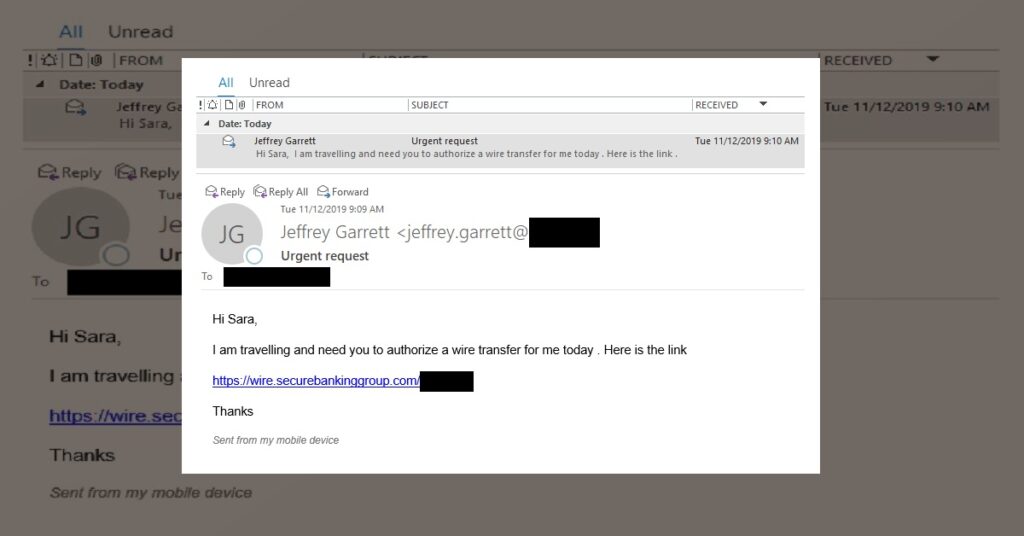

How to Spot a Spoofed email
One of the biggest things to look out for is what may be considered social cues. A social cue can be most described as a circumstance that does not otherwise fit. Because in a spoofing email, the scammer may be able to copy a victim’s email address.
However, the scammer will most likely never be able to construct a conversation using the same words and pattern as the authentic owner of the email address. This is because most scammers involved in spoofing do not know the victims. They use whatever addresses they can get their hands on that can also accomplish their particular scam.
How Spoofed emails Work
For example, if they are trying to scam a bank, they will use the email address of an executive they can access online. This does not mean that they know this particular person. This also means they do not know what kind of words this person uses or how they talk.
With this in mind, it can be important to look closely at what people say in spam emails and know if it seems to be something they would say.
Are they using terminology that is appropriate for fair education and position in a company? Is what they are asking something that is out of the ordinary such as a large transfer of money.
How to Stop Spoofed Spam Emails
You don’t. Why? The reason you cannot prevent this type of threat at the user level is that control of your account is not necessary. This kind of threat depends mostly on prior education and damage control.
If you think your email address if compromised, we have an article here about how to remove your email from the dark web.
What I mean by prior education is in the case of an organizational email system. Educating students or employees, or other users about the typical types of spoofing email can help. They may be able to recognize a spoofed email before an attack is successful. Damage control occurs after a spoofing attack becomes apparent.
Once you are aware of the problem, early intervention is key. This can include reaching out to all of your contacts to warn them of a potential threat. Also, suggest they disregard any previous spam emails recently sent to them by your account.
Prevent falling victim to spoofed emails by attention and detection.
Educate your friends, family, or employees. Other than that, simply move these spam emails into your spam folder or junk folder. The name of the folder and how you do it depends on the email service you use.
Types of Spoofing
The three most common types of spoofing are email, website, and caller ID. This article focuses mostly on email spoofing, but the concept with the other type remains the same.
Website spoofing typically mimics the login pages of major companies or financial institutions. The URL at the top of the page is very similar to the legitimate website. The only difference may be the smallest misspelling.
Another tactic is the use of double or triple letters in the name that can be difficult to spot. Below is an example of a website spoofing Google.com. You can easily see there are far too many “o”s in the website address. Also using different domain extensions other than the expected “.COM” is more noticeable.
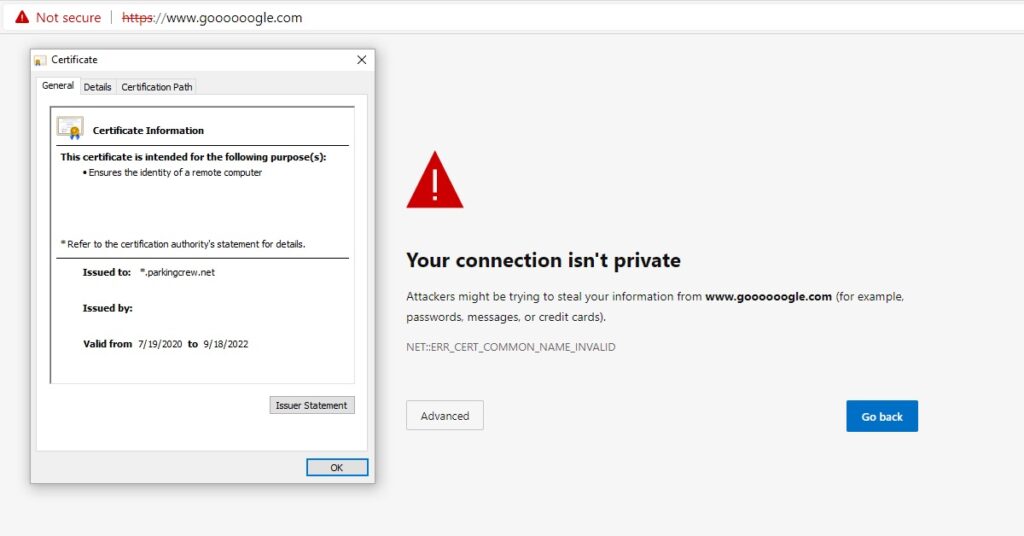

These fake sites copy the real websites in content except they alter them either to make fun of the source or steal sensitive information.
Caller ID spoofing is most common with robocalls or spam phone calls. It seems most of the spam calls I am currently receiving involve a voice with a foreign accent telling me my car warranty is about to expire.
The only problem is they are not aware I drive a vehicle that is ten years old. The fact that I do not have any warrant does not stop the calls. Instead, they are likely trying to solicit buying for expensive or nonexistent insurance.
Other than spam, scams are another likely purpose for Caller ID spoofing. For further reading on the topic of Caller ID, read our article Should I answer No Caller ID.
Start blocking wanted calls with RoboKiller.
Spoofing vs Phishing
There are some similarities with spoofing and another term you may be familiar with. That cybersecurity term is phishing. The main similarity is that in both circumstances, the scammer is using deception. They are basing the scam on using the credibility of someone else.
For example, if a person you do not know sent you spam emails with a link you will be much less likely to click on it. If you do recognize them, or in these cases, think that you recognize the sender, it may convince you to click the link.
The difference between spoofing and phishing is simple. Spoofing is the act of impersonating someone else through phone or digital communications.
The reasons vary from spam, pranks, to other purposes. One of those purposes is phishing. Phishing is using a tactic such as spoofing to impersonate another to steal sensitive information such as passwords.
Sniffing and Spoofing
We have already covered spoofing extensively in this article. With that in mind, sniffing refers to intercepting electronic data as it is being transmitted. These pieces are generally called packets. As the sniffer program listens to and records this data, it can be read to discover what commination can is being transmitted.
As opposed to spoofing, sniffing has nothing to do with impersonation. Instead, sniffing is digital spying while spoofing is identity theft.
Is Spoofing Illegal?
Depends on who you impersonate, your intent, and local laws in your area.
For example, if you use someone else’s name or email address to send a prank to a fellow coworker that does not cause emotional or financial harm to anyone, you would be unlikely to be prosecuted.
First, the victim would have to be willing to file a complaint as well as cooperate.
Next, the police and prosecutors would have to be willing to spend money and resources to pursue the prosecution which would be unlikely to be worth the effort.
Finally, with no real boss and most laws not up to date with most online activity, your actions would have to meet an established unlawful act.
Hacked or Spoofed Email?
There is often confusion surrounding what kind of security threat is involved when emails are sent from addresses the valid owner did not authorize. Most people unfamiliar with spoofing assume they are all victims of hacking.
However, there is a distinction. When your email address is spoofed, your account is not affected or even involved in any real manner. A hacker has not gained access to your account or has access to your login credentials.
Instead, they sent the message listing your address as the sender without ever needing access to your account. By contrast, if your account was hacked they would have control over your contacts. They would also have control over all of the messages associated with it. This would mean the hacker either knows your password or bypassed it.
Difference between Scam & Spam Emails


What are Spam Emails
Spam email typically consists of multiple unwanted and unsolicited advertisements for a legitimate product or service. Sometimes your phone number or email address can end up on a spammers list because you purchased a product or signed up for something unrelated. When that happens, your information may become compromised.
Depending on the spammer, the spam can be minor and easily stopped or it can be constant. There can seem to be no other way to stop it but to block the senders.
An example of spam can probably be found easily in the junk folder of your email. Some spam that I get involves website boosting since I own a website. I do not sign up for these advertisements. But through the course of purchasing a website and signing up for programs associated with it, my email address is obtained by the spammers.
What Scams are
Scams can mirror spam in appearance, but typically the end goal is different. Scams do not advertise a legitimate product or service. Instead, their design is to trick or deceive.
An example of a scam would be an advertisement for winning a prize or a gift. The scammer would first make the person pay a fee or taxes. In reality, there is no prize to collect and the victim can not get their money back.



Conclusion
Scammers use spoofing to send you spam you are more likely to open. This method makes it look like the emails are coming from your contact when they are really not. Think of these scammers as con-men who build your trust by stealing the email addresses of your friends and family.
There’s not much you can do about these emails. The best thing is learning how to identify them so you don’t open attachments or links. Either of these is likely to include viruses or malware that will further cause you problems.
Finally, by sending this article to your contacts they can learn how to avoid falling victim to spoofing scams.

