A slowloris attack is a serious matter. Denial of service attacks like this can make your server grind to a halt. Find out which servers are most vulnerable. We will also cover everything you can do to help prevent and mitigate a slow loris attack.
Defend against a Slowloris denial of service attack by increasing the maximum connections allowed. Also restrict multiple connections from one IP address and limit allowed connection times. Use a less vulnerable server like Cisco CSS or product such as CloudFront for accelerated caching.



Table of Contents
How to Prevent Slowloris DOS Attack
If you need help with a slowloris attack on your server, this next section is for you. There are many tactics you can use to prevent a slowloris attack.
Be warned no prevention is foolproof. Prevention does not mean elimination. There is always a threat. Continue to monitor your servers for vulnerabilities for the best protection against slowloris.
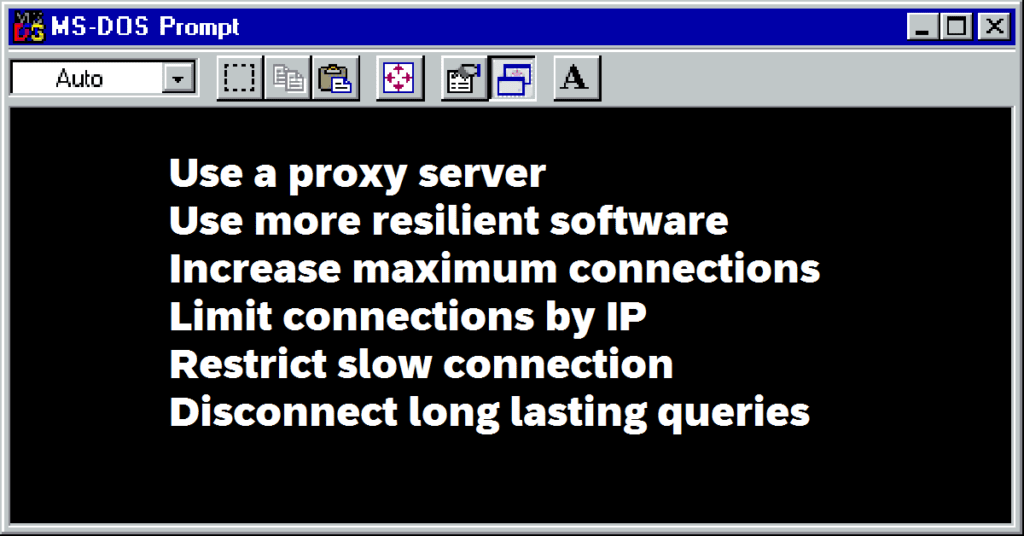

Use a proxy server or caching accelerator (Amazon CloudFront)
This protects your server from direct contact. The proxy acts like a sacrificial lamb. It locks up and crashes but can’t pass that onto your server. Meanwhile your server is available to use another proxy to continue its normal function.
Use a more resilient server (IIS or Cisco CSS)
Slowloris affects Apache servers disproportionately more than others. So if you can’t beat it, avoid it. Use another type of server such as Cisco’s CSS. Tests have shown it’s better at handling these kind of threats.
Increase maximum allowed connections
Change the number of clients the server allows to connect. Increase this number to meet the demand. That way actual users may still be able to connect. Your lag time will suffer but it can mitigate ugly errors.
Limit number of connections by one IP address
Play some offense by anticipating similar attacks. You can do this by allowing only one or a few connections from the same IP address. It can be an inconvenience for people connecting from schools or large organizations. But the alternative of a locked up server would be worse.
Restrict connections with low transfer speed
This sounds like an obvious solution. Slowloris attacks involve painfully slow connections. Eliminating these connections can help. But be careful not to alienate people connecting from other regions. This has the potential to block a lot of legitimate traffic if it’s too strict.
Limit amount of time connection can stay active
Slowloris attacks occur over an extended amount of time in order to keep the server busy. Because of this, disconnect users who tie up sever resources for too long. This does not prohibit real users from reconnecting. But it can trip up the slowloris program because it’s not a brute force type attack.
DOS Attack Remediation
The above tactics are how to mitigate a slowloris attack. But not every defense is 100%. Your server can still be affected by an attack. If your server does experience an outage, below you can find remediation options. Remediation happens after the attack occurs as a dos attack fix.
Protect Apache Against DOS Attack
Apache 2.2.15 and newer all come with the module mod_reqtimeout. This is touted as the official Apache slowloris fix per the original developers. If you are not interested in a server change or cannot avoid Apache, this could be the best slowloris protection for you.
This next suggestion may be obvious to some. But often it is taken for granted. Keeping software updated is always a best practice for all types of software. Complacency makes us vulnerable. Keep an eye for the latest updates. Once you confirm your system is compatible make the change.
DOS Attack Tool
CloudFlare
CloudFkare has a purpose-built feature specifically designed for ddos attacks. Not only that but they identify slowloris by name. Both free and paid options are on their site. The free options do provide some limited protection from ddos attacks. These limitations are based on the size and intensity of the attack.
AAS Shield
This operated under the umbrella of Amazon CloudFront. The AWS Shield automatically protects against ddos attacks such as slowloris. CloudFront is a content delivery network that provides proxy servers which serve cached content to users on the internet. With CloudFront slowloris doesn’t stand much of a chance. There is a flexible payment model used by Amazon so you can pay as you use it.
Wireshark
Wireshark is adequate as a potential solution for anyone on a budget. They provide a free and open source packet analyzer. But you get what you pay for. It is an analyer as opposed to a solid solution for preventing an attack.
What a Slowloris Attack is

In technical terms a slowloris attack is a form of ICMP flooding. But there is a more basic way to explain it. An online slowloris dos attack tries to shut down web servers by overwhelming them. They accomplish this by sending requests to a server purposely slow.
These requests keep the connection between the attacker and the server open. Internet servers can only have a certain amount of connections at one time. Otherwise they become overloaded and can’t handle all of the requests.
When the server is too overloaded and someone tries to connect, it can’t. The server is unable to send the information. For a website this means the user would see an error such as a 404 page.
This is the key premise of a DOS or denial of service attack. Service to legitimate users is the denial of access to the server or website.
What is Meant by Slowloris
The origin of the name slowloris in DOS attacks comes from a slow moving primate found in Southeast Asia. This is an alternative to the sloth which is overused when referring to slow animals. The name slowloris gives this type of attack a unique identity.
How Slowloris Works
A slowloris vulnerability mainly affects Apache web servers, but also includes others. cPanel users often have Apache as its underlying server. If you use cPanel, check if Apache is running. If so, slowloris is something you should be concerned about
Slowloris is effective because the software regulates the speed at which the attacking computer communicates with the target server. Normally your computer would want to request and obtain information from a server as quickly and efficiently as possible. The design of slowloris allows an attacking computer to tie up the connection for much longer.
Rudy vs Slowloris
RUDY stands for RU-Dead-Yet. They are very similar but slowloris provides less data. RUDY starts sending both a header and body of a message to a target server. Slowloris only sends the beinginig of a header. For this reason, slowloris wins the race (of being the slower attack).
LOIC vs Slowloris
An LOIC attack stands for Low Orbit Ion Canon. The main difference is LOIC is not powerful enough to be effective with a single attacking computer. It requires a distributed effort among a group of participants. This is also known as a distributed denial of service attack (DDOS).
Slowloris vs Syn Flood
Slowloris and a Syn flood are very similar. But a syn flood deals with the very beginning of the connection with the target server. Instead of sending any real message, it opens the lines of communication and fails to complete. This is like a tap on the shoulder then no follow-up. Syn flood would be considered a slower attack than the slowloris.
Example of a Slowloris Attack
An example of a slowloris attack happened in 2009. During the 2009 election in Iran, government websites were attacked with slowloris. This was done as a result of protesting the violence in the area.
Why Slowloris is Used
The justification for slowloris usage varies. As seen above, its use can be for political protest. Hackers have many motivations. However, often they see it as a way to combat activity the hacker does not agree with. Other hackers may use it as financial gain. Ransomware is can be a way to solicit money from targets in return for restoring functionality.
Legality in the U.S.
The use of slowloris and other DOS attacks are a federal crime. They are illegal under the Computer Fraud and Abuse Act. If they charge and convict you of this crime, you face a possible sentence of 10 years in prison and a $500,000 dollar fine.
This kind of activity is also illegal in various states. States such as Pennsylvania have laws which describe it as Computer Intrusion or Computer Tresspass.
Ethics – Ethical Hacking
Not only is the use of slowloris a crime, it is also morally wrong. Ethical hacking deals with hacking to identify vulnerable systems so you can fix them. It can also include gaining access but not taking action.
However, DOS attacks such as slowloris create a serious impact. Server downtime can be very costly depending on the target. The loss of potential sales and the price for cyber security experts to fix it add to this cost.
How to Detect a Slowloris Attack
I recommend checking your systems for vulnerabilities before problems arise. To detect the potential for a slowloris attack, there are online tests such as port scanners. Below are a few of the top options I find useful.
Vulnerability Check
Metasploit
Owned by Rapid7, the Metasploit Project preforms penetration testing to see how your server would handle a real attack. You can use the results to fix vulnerabilities.
Free software download directly from the Rapid7 website https://www.metasploit.com/download.
Slowloris vs Slowhttptest
Slowhttptest is a penetration tester. It simulates a denial of service attack. The best part is it’s a free and open source option for troubleshooting. It can identify lapses in security ripe for possible slowloris ddos attacks. However, it does not fix these problems for you.



Conclusion
By implementing the above mitigation techniques you are as safe from a slowloris attack as possible. However, new exploits are popping up all the time.
You can check out our recommended VPN provider SurfShark here.
I suggest you set a reminder on your calendar to conduct regularly scheduled tests for slowloris dos attack vulnerabilities.
Another recommendation I find particularly helpful for finding vulnerabilities is to search for Common Vulnerabilities and Exposures. This can be as simple a as Google Search with “CVE” and the name of the software you use. Check these resources so you know what vulnerabilities to anticipate.
Finally, we have an article that explains How do hackers find vulnerabilities. Thanks for reading.

