If you are concerned about the security of your code, use an obfuscation program. The JavaScript obfuscator will change and obscure the code. This will make it undiscernible by the naked eye and ensure it is hard to be reverse-engineered. In this article, we discuss different options and explain which program is the best for you.
ProGuard is the best JavaScript obfuscator. It is the most advanced tool and boasts many additional features such as code optimization. This software is not only free, it is open-source and trusted by a majority of the programming community.
Table of Contents
Best Javascript Obfuscator
ProGuard is the most popular choice for Java bytecode. Typically for me, popularity contests are not important. But sometimes it can be telling. Often there is a good reason why so many people choose the same product such as ProGuard. I believe in this case it is because it is the best choice when considering all factors.
One great thing about ProGuard is it’s free to use. This means there’s no risk for you to try it. If it doesn’t work out for any reason you’re not out any money.
Another great point is that while it obfuscates, it also shrinks and optimizes your code too. This is a great extra that some of the other tools just don’t offer.
What I believe is the best feature is the fact that it is opensource. This allows for a great deal of input from users. As a result, security is improved as vulnerabilities are tested and mitigated.
What this also means, is that there is a large community of fellow programmers who can be used as a key resource when the time comes to ask for assistance.


How to Use JavaScript Obfuscate
Obfuscation Techniques
Use of Spaces or Lack Thereof
This is where the presence or absence of characters creates designs. they are limited in complexity only based on the imagination of the programmer. For example, if the programmer was a fan, they could arrange letters numbers, and special characters in a specific order to give the effect of a cartoon character of their choosing. Obviously, this goes beyond simple cartoons and the designs are limitless.
Substituting Keywords
These are words of phrases that typically stand out to a critical eye. They are typically names that are indicative of what action is being taken in the code.
For example, if the keyword is “text”, it likely means that what is to follow is likely a string of characters in word and sentence format much like the page of this article. In obfuscation, this keyword may be changed to either something unrecognizable or deceptive. If you rename this keyword to vacation, its intent and function would be obscured.
Deceptive Variable Names
Much like the example above with keywords, the same can be true for variables. Instead of changing for disguising the names of keywords, the functions that store information can also be obfuscated in the same way.
Camouflaging Comments as Code
This technique is another form of trickery. While compilers read the code and ignore comments, humans typically read comments as they are an easy way to explain the code in simple terms. It is possible to format comments in a way that makes them appear to be active code. What this really does is it has the effect of distracting the viewer with irrelevant content.
For example, if I intend for my code to display a message on the screen, I could add comments that appeared to be code that a viewer thinks is referencing unrelated activities such as language translation. This way, the viewer must sift through the code carefully to understand what is important and how the code actually functions.
Obfuscation Example


Google uses Javascript on their site. Go to the main search page and right-click anywhere on the white space. Click View Page Source. There is also a keyboard shortcut in Microsoft Edge, Control + U.
Detect JavaScript Obfuscation
Obtain source code and look for clues such as missing comments or one-letter variables. Most people try to make their code look organized and easy to read so they can find distinct areas for reference later when changes need to be made.
How to Read Obfuscated JavaScript
JavaScript Obfuscation Reverse
To deobfuscate JavaScript, you have to use a tool much like when the code is obfuscated, to begin with. A good rule of thumb is if a program obfuscates it, it needs a program to deobfuscate it. There are contests for people to reverse obfuscation ‘by hand’. The difficulty threshold is lower than what would be seen ‘in the field’ or in a real-world application.
Obfuscation Decoder
dCode’s Javascript unobfuscator is the primary tool that I would use in this situation. It just so happens that I do not have much use for it. Most people might think that subverting obfuscation can only have nefarious purposes.
However, what comes to mind are the situations where there is a changing of the guard. What I mean by this is there is a personnel change where the original programmer is no longer available for assistance.
This kind of situation happens all the time. Companies hire new programmers who need to access and learn the last programmer’s code. A company may retain the rights and usage of the software long after the original programmer is no longer working there. At that time if the code needs to be fixed or modified option station would make that impossible.
How does JavaScript Obfuscation Work?
What is JavaScript Obfuscation?
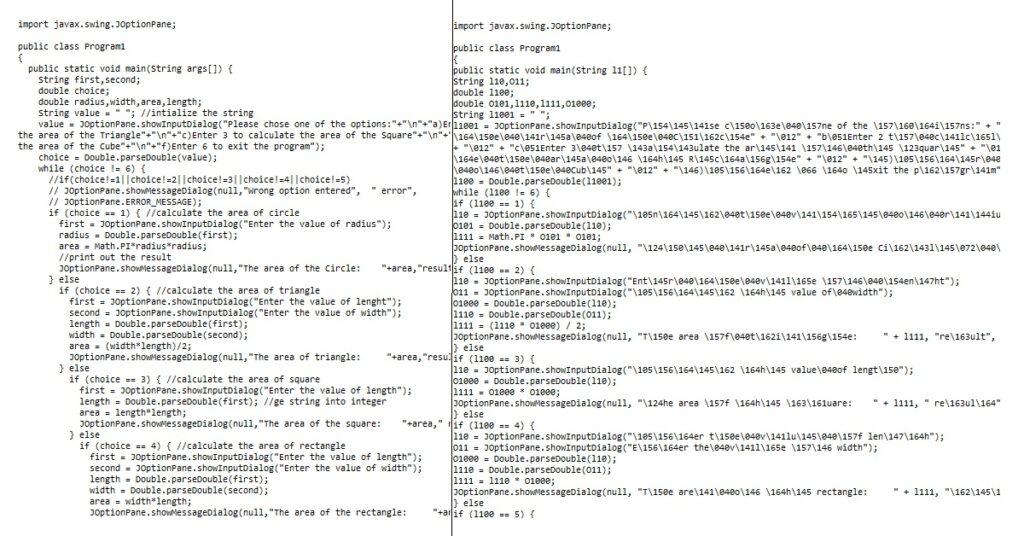

Obfuscating in programming terms means changing the source code to make it difficult or even impossible for humans to read. However, computer compilers are still able to understand its purpose. Otherwise, it would render the code useless. Once they decipher the meaning of the code, they can then proceed and run commands. The results gained by the obfuscated code stay the same.
Why to use it / Why it is Important
- For fun (Contests)
- Faster load times (Minification)
- Protect information sources (Trade Secrets)
- Increase security (Deterring Hackers)
- Prevent Virus Detection (For Evil)
There is no particular order to this list. The first reason on our list is for fun.
People have fun in a multitude of different ways. When you are a computer programmer, one way you can entertain yourself and others like you are by having friendly competitions. These contests will test each other’s skills and see who has the best technical abilities. Besides, some of the ways that these coders alter the structure of their code can find entertaining.
For example, we will talk about the use of spacing and whitespace in between pieces of code. These designs provide an unlimited amount of ways that a programmer can express themselves.
Faster loading times for the code is yet one more motivation for the use of obfuscation. Because this practice Simplifies the code by removing unnecessary data where necessary, it takes less time to process the shorter amounts of characters.
This is in direct contrast to what most people would assume to be true. Because obfuscation makes the code more confusing to the human eye. However, to a compiler that runs the code, it makes perfect sense.
Obfuscating for Cybersecurity
The next, and potentially most important reason is for the protection of data. user interfaces make the way you see computer programs look pleasing to the eye. They also make the way you interact with programs much simpler and easier to understand for the user.
However, most people do not see the coding behind the scenes. This programming coding to the untrained eye can appear to be And confusing. But unfortunately for programmers, this code can actually be found client-side in most applications.
Because of this, it can be subject to scrutiny from people who wish to steal this information. Simply the work performed to develop the code is worthy in and of itself of being protected from copying. Furthermore, sensitive business information can be transmitted through the code which also wants to be protected, such as internal data and trade secrets.
Similarly to the above reason, programmers are motivated to protect from hackers deciphering their code. as opposed to simply copying the code or trade secrets, these hackers if they are able to by-pass the obfuscation may be able to Ben exploit the code for more nefarious reasons. This reason can include the theft of trade secrets.
However, it can also mean obtaining customer sensitive information or worse yet, taking over the program itself. They would accomplish this by changing or inserting new code in order to manipulate the way the program operates for it there desired result. Finally, this results is typically By the release of information such as what you would see in a data breach.
Dark Side of Code Obfuscation
Lastly, there is an unfortunate way that programmers use obfuscation. Maybe it should come as no surprise because best practice is all about misdirection and privacy.
In my experience, I’ve seen that often times these kinds of circumstances lead to criminal activity. If you read my article on this website about the Tor browser, you will see in more detail what I am talking about.
Briefly, criminals see an opportunity to hide their identity and think this is a ripe circumstance to commit a crime. As it is related to obfuscation, oftentimes malicious code is hidden. If a hacker creates a code that, once run acts as a form of malware, obfuscating the code would make it difficult to understand the function of the code. Therefore identity it as malware would be more difficult.
Obfuscate vs Encryption
With Encryption, code is changed into a pattern known only by the person or program encrypting it for the purpose of keeping it secret.
They are similar because they both share a similar goal. That is to prevent hackers or stop the theft of information.
There are ways they are different too. Obfuscation can include encryption as one of the many techniques. Additional techniques are listed earlier in this article. Encryption, on the other hand, is the way in which code can be obfuscated. Encryption also takes this a step further by requiring what can be considered a key in order to hide the data. That is why encryption is used so frequently in electronic communications.
If I sent you an obfuscated code, with the right know-how and software you would be able to defeat it quite simply. However, the encryption would be nearly impossible to defeat. That being said, encryption is a more secure method to secure data. However, it also comes with some associated risks. One risk that encryption cannot defeat is social engineering.
For example, the key to my house prevents unauthorized entry. However, if someone steals the key or tricks me under false pretenses to letting them in, the key or encryption would be bypassed.
Is Obfuscation Effective?
Perhaps you have ever heard someone say that locks are for the honest. What this typically means is that no law or form of obfuscation is foolproof. It would seem that whatever kind of security a person can think up, another person or perhaps a computer can counter.
As mentioned above, hackers find other ways such as social engineering in order to infiltrate systems and bypass security.
This begs the question of why even bother using these measures. The reason is they work for a majority of the situations. The lack of them I believe would be utter chaos. They can be a successful deterrent and even stop some hackers completely.
Obfuscation alone is not effective web security. It is one layer of the onion as referenced in network security. Each layer reinforces the protections. By implementing other types of security, your systems are most secure.
ProGuard Obfuscator Alternatives
FixScam doesn’t benefit from your choice of JavaScript obfuscators. The commission on a $0 sale is $0. Since ProGuard isn’t right for everyone, here a few other options.
The JavaScript Obfuscator by Timofey Kachalov can be found here at their website https://obfuscator.io.
DashO by PreEmptive can be found at https://www.preemptive.com/products/dasho
Semantic Designs http://www.semdesigns.com/Products/Obfuscators/JavaObfuscator.html
Conclusion
The best JavaScript obfuscator is ProGuard. It’s free so there’s no risk to try it. It’s also opensource which adds to its security. There are also other benefits such as it optimizes the code. Its popularity among programmers is another stamp of approval.
Here’s a direct link to GuardSquare’s ProGuard. You can read more about it, download the program, and join the community.
Do you know of a better program? Share your favorite in the comments below.